
A few years back, the world witnessed one of the biggest data breaches ever happened. Equifax, a consumer credit reporting agency, was the victim of this scenario. Many personal details of consumers, like names, passwords, email ids, etc., were at stake for over a month spanning from mid-May to July. Well, it was only just one of its kinds, and hackers are continuing their job till the date successfully. Recently, the data breach controversies of Facebook, Google, and other social media platforms have also made us think even more about the security of our privacy. And this is why you need to look for ISO 27001:2013 certification.
Rather than catching the culprits, the best we could do is to prevent it from happening from all the sources. This single aspect marks the importance of certification from credible sources like ISO. So that consumers can have services from a more trustworthy source. This is one of the main reasons why companies like INFOLKS dealing with highly sensitive data have to be certainly certified. Since image annotation is our primary service, and processes inculcate image labeling through various annotation techniques. The need for a highly secure framework was also high. Understanding this, we too had acquired ISO 27001:2013 certification recently.
With lots of certification choices available, you may choose the best one for your services accordingly. GDPR is a considerable one in this aspect, however, ISO standards have more global acceptance and deal with the handling of any data. So are you planning to get ISO certified? If so, then first we need to know a bit about ISO, and then we can have a detailed discussion.
What is ISO?
In simple terms, ISO is a non-governmental organization that underlines the standard frameworks needed to be adopted in organizations. ISO stands for International organization for Standardization. However, the word ISO is not an abbreviation for the latter. It was derived from its Greek version “ISOS”, which means Equal. This was done so that the term ISO remains as it is, and can avoid formulation of variety abbreviations resulting from the translation of it into other languages.
They are the world’s largest developer and publisher of International Standards that are applicable in various aspects. The body consists of several standard bodies, each representing a country. A total of 160 countries participate in outlining these best practices. Each standard body is considered an accreditation team, having the authority of selecting certification bodies and consultants. We will be discussing the detailed hierarchy in the upcoming sections.
ISO Standards
Origin of ISO standards dates way back to 1946 (after World War II). But truth be told, the system came into action in 1928 and existed till 1942 in a different name, the International Federation of the National Standardizing Associations (ISA). This sums up the history of ISO. From 1946 onward, the organization has developed, coordinated, revised, amended and interpreted a total of 22,000 standards till the date.
As mentioned above, ISO standards are made applicable to various entities, like companies, corporate, freelancers, etc. And the standards also span around a number of frameworks used for enhancing quality, information security, management systems, etc. Some of the basic and popular ISO standards that companies adopt are:
- ISO 9000 family: An ISO standard for ensuring service quality. The popular standard ISO 9001:2015 implements a Quality Management System (QMS).
- ISO 27000 family: ISO standard for ensuring data security system. One of its standard ISO 27001:2013 involves the implementation of the Information Security Management System (ISMS).
- ISO 14000 family: This set of standards relates to the environmental system. One of its standards helps organizations to implement the Environmental Management System (EMS).
Let’s skip these history classes for the time being and discuss the matter that really matters.
The Hierarchy
ISO hierarchy is a three-level system resembling a tree-diagram. They have a more centralized structure with a central body monitoring the whole system, called the International Accreditation Forum (IAF). The body selects different accreditation bodies representing various countries participating in the process. These standard bodies are responsible for drafting, amending and designing the necessary worldwide standards. Different countries have different accreditation bodies. Below is a list of examples:
- UKAS — UK based accreditation body
- IAS — US-based accreditation body
- ANSI — US-based accreditation body
- NABCB — Indian based accreditation body
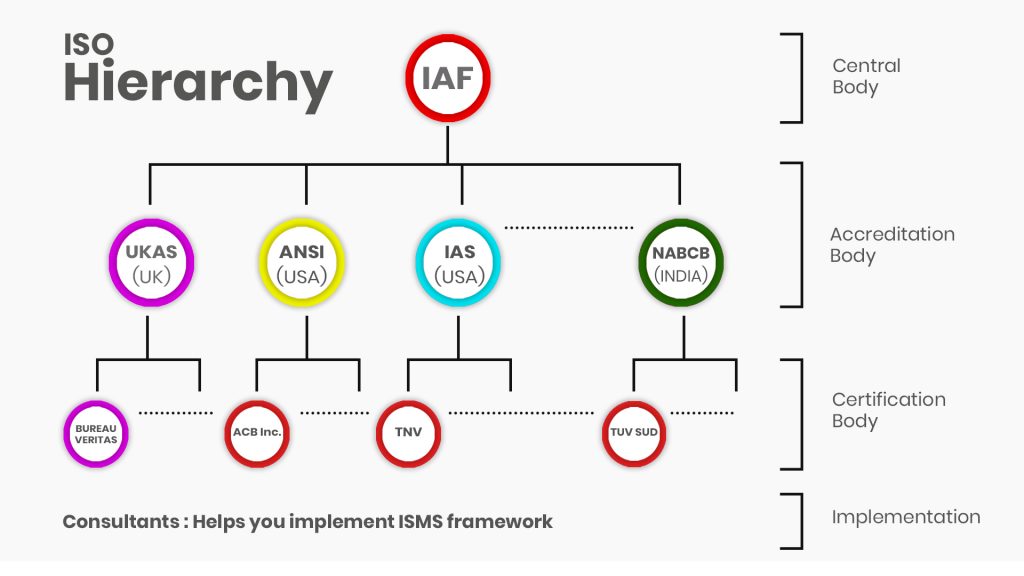
These accreditation bodies in turn choose the certification bodies, usually third-party organizations. These authorized entities are only capable of issuing a certificate, and no other parties are responsible for this task. Some common names on the list are Bureau Veritas, TNV, etc.
ISO in Data Security
Data security is one of the most sensitive topics and the biggest hurdle that any organization confronts. No matter how well you have arranged your security management system, services seekers always value your services with trust and credibility. If you are not that credible enough, so that any stranger can believe in you, your market position can always be vulnerable. This is because data has become a powerful tool now, unlike the traditional scenarios. Now data, or more precisely big data, can help us infer various sensitive features that may even account for his/her personal interests.
So how can you be more credible in front of your service seekers? How can you storm the markets with this exceptional trait of your company? Yes, getting certified is one of the key factors. There are various certifications and attestation that can help you entrust data security in your clients. ISO certification is one among them. As said above, ISO standards are further classified into different families based on their field of application. ISO 27000 family standards enable data/information security. Among this class of standards, ISO 27001:2013 is the most important standard and is the one to which usually organizations are certified.
Why ISO 27001: 2013?
Even though ISO 27000 family standards are said to be dealing with information security and privacy, ISO 27001:2013 is considered to be a cornerstone member of the family. This is because ISO 27001 is the standard that defines the requirements for implementing the so-called secure framework. Information Security Management System (ISMS) is the secure framework outlined by this standard. Rest, all of the standards are considered to be the supporting agents of the former one. For instance;
- ISO 27002 contains the code of practice for information privacy control.
- Design and implement the concept of ISMS given by ISO 27003.
- ISO 27008 details on how to assess controls.

The list goes on and sums up to a large set of standards. The majority of them act as a supporting document for the implementation of ISMS. At the same time, ISO 27001 is the core standard that implements this framework, and usually, organizations are certified against this standard. In order to understand the complete ISMS framework, all of its standards have to be evaluated. A basic definition of ISMS can be.
How to Implement ISMS?
Getting ISO certified is way too simple. Time is the most important factor in the process. Before getting to know how to get ISO 27001:2013 certified, a clear picture of ISO hierarchy is a must.
Before applying for the certification procedure, the ISMS framework has to be implemented successfully. Detailing the ISMS framework and its implementation can be lengthy and tiresome. This is why you always have to seek help from experts. According to hierarchy, in most cases, certification bodies only certify the organization against the ISO standards. In order to implement the framework, you will need to meet a consultancy/consultant. Along with the framework, they will also help you prepare a detailed report on the same, a needed document for ISO 27001:2013 certification.
Beware Of…
If everything goes in its way, you will be getting certified. But how will you know if you are cheated? For that, you must be aware of the fraudulent activities. Mostly this trait is accompanied by consultants. Either they might be unaware of the ISMS framework and implement the wrong system, or they may cheat you with some lame certificate.
So how do you make sure you are on the right path? Before even starting implementation, you must ask the consultants regarding the certification body and their accreditation body. If their response is not genuine, you can rule out them in the first place itself. For example, TNV has issued our certificate, an American certification body accredited by IAS. Details of certification bodies are available on the accreditation bodies official site. And can be cross-checked for any references.
But frauds are too clever, they know all these things and there is still a chance to cheat you. Once an organization is certified, they receive a soft copy and hard copy of the certificate. Once you receive your soft copy, check the authenticity of the certificate on the certification body’s official site. The copy will be containing a unique certificate number. Use this for your reference. Nowhere on the internet, you will be able to find these details. Make your payments after this, and wait for your hard copy to reach you.
Benefits of ISO 27001 Certification
When an organization is ISO 27001:2013 certified, there are several benefits for the company itself. The primary one is the privacy of data it handles, no matter wherever it lives. With the ISMS framework implemented this is one of the best assurances that an organization can give their service seekers. Another one is the less chance of penalty. With reduced risk of data breach, organizations need not bother much about this aspect.
Reduced audit frequency is another benefit of this certification. Once your company is certified, you need to renew it once every 3 years. During this time, you will have to carry out a complete audit and renewal procedures. Unlike other attestations or certifications, this can save you more time and money. Finally, promotion is the last benefit available in this scenario. Being certified improves the company’s trust and credibility well enough in the market. And hence increases its market value, productivity, and acceptance. But before proceeding, you must also be aware of some do’s and don’ts while promoting this aspect. A usual one is a restriction in modification or usage of the ISO logo. A common mistake is usually spotted. You can make and use your own logo without making use of the ISO logo. Also, you are not authorized to write “ISO certified”, instead you should clearly state “ISO 27001:2013 certified”. This is because a third party issues the certificate. Which makes the former usage wrong info. Similar to it, there are various other factors to be kept in mind. Read here to promote your ISO news effectively.
INFOLKS and ISO
In the month of July, Infolks was ISO 27001:2013 certified. Since our works mostly dealt with images as the data, our service seekers were cautious about its secure handling. Thanks to ISO certification, which has enabled us to show more about ourselves and gain considerable trust and credibility in the market. Above all, we have also won hearts. For more reference, view our certificate. Getting certified by an authorized party is the best achievement that your organization gains.
Are you planning to carry out your annotation requirements in the most secure environment? The above explanations are evident to prove our system’s security. Contact Us for your further queries on our various image annotation services.
Very useful information!