

Get all your annotation requirements done for just $3.5/hr.
Try our
free demo services Now


We respect data security the most and ensure that your information gets the same respect.
How we assure?
How we assure?

We are ISO 27001:2013 certified and our environment is compatible with EU GDPR standards.

All our services are done by hired in-house employees at our secure work spaces. Services are neither crowdsourced nor outsourced to third parties.

We make our in-house employees to sign a legally valid NDA so as to ensure secure handling of your data.

We have implemented high standard firewall systems on our networks so as to prevent any form of cyber threats and attacks. Internal data transfer are also carried out through highly secured LAN networks.

With a biometric office entry-exit systems, we ensure that only authorized persons enter the office environments.

We have setup a 24/7 recording surveillance system for constant monitoring over workspace.

Mobile phones or any other type of electronic and data storage devices are completely restricted in office premises.

Data that we receive are downloaded and stored in highly secured computers to which only authorized personnel has access. Once the project is over, the same data are retained for another 14 days for any post project needs. After which the data is completely removed from systems.
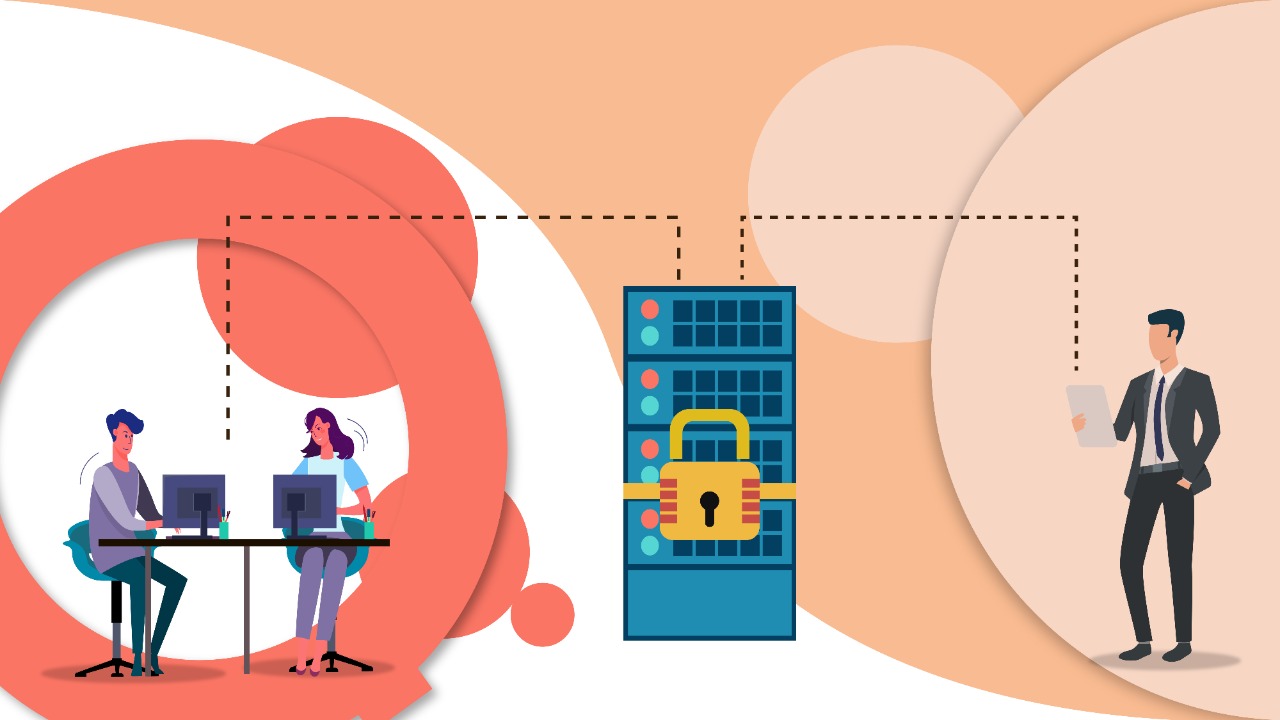
Project data are received from clients through secured cloud storage. The shared data are then stored in a well protected master computer. These data are then passed to annotators using highly secured LAN networks. No external devices like hard disks, pen drives, etc. are used for internal data transfer. The labeled data is then collected from employees using LAN networks and stored in the master computer. Labeled data are submitted back to clients using secured cloud storage.
A set of data security officials along with qualified lead are summoned to form a Data Security Wing for implementing accurate data security measures
We respect and value your privacy
This privacy notice discloses the privacy practices for INFOLKS. This privacy notice applies solely to information collected by infolks.info. It will notify you of the following.
Information collection
We are the sole owners of the information collected on this site. We only have access to/collect information that you voluntarily give us via email or other direct contact from you. We will not sell or rent this information to anyone. We will use your information to respond to you regarding the reason you contacted us. We will not share your information with any third party outside of our organization.
Your access to and control over information
You can always see what data we have about you, change/correct it, have us delete it and express any concerns you have about our use of your data at any time.
Security
We take precautions to protect your information. When you submit sensitive information via the website, your information is protected both online and offline.
All the information you give to us is encrypted and transmitted to us in a secure way. We use encryption to protect sensitive information transmitted online, we also protect your information offline. Only employees who need the information to perform a specific job are granted access to personally identifiable information. We do not partner with anybody else to provide the services and there is no chance of your information being shared with the outside. The computers/servers in which we store personally identifiable information are kept in a secure environment. All of our computers are protected with the latest version of the firewall.
If you feel that we are not abiding by this privacy policy, you should contact us immediately via telephone at +91 7025889911 or via an email at
info@infolks.in
This website contains links to only our subsites infolksgroup.com and infolks.info/blog/. These two sites also practices the same privacy policies.